A Guide for Preparing to Leave Your Numeric Legacy
When someone passes away, managing his or her legacy can be challenging. Younger generations are building a numeric legacy that can prove to be impossible to manage. See how an emergency kit can alleviate the burden and make your life easier.

The Digital Legacy Management Guide is now available on Gumroad
In challenging times like we are currently in, death becomes an everyday subject. Losing someone you love is painful. When we pass away, it can be a major burden for the family to manage our legacy, not only in the physical world but in the numeric world too. Preparing to leave your numeric legacy is something you should be considering doing, but how do you address this challenging endeavour?

I wanted to write something like this for a long time. Now, here it is. It’s been a long journey. The idea for writing this guide came up after briefly touching the matter in “Managing the Elderly’s Numeric Life“. When I wrote this piece, it was about managing the numeric life of my living, but very old parents. I had to ask myself: “when they will pass away, how do I prepare their numeric legacy?”. The same question applies to me and everybody else for that matter. After someone’s death, how do survivors get access to the numeric legacy of the diseased? How can you recover photo libraries? What about social networks like Facebook or Instagram, how do you access them?
As more and more things happen in the virtual world, the numeric legacy of someone grows. Over the years, we subscribe to services like iCloud and pour things in them. Our parents accumulated physical souvenirs, but the following generations are building a numeric legacy with a lot of data in them. We need to prepare how we will leave it behind. This is what this guide is all about.
Read me first
This guide is not about helping people writing their testament, nor is it trying to replace a testament, far from it. Consider this as a complement to your will. Also, this is an Apple-centric guide, but most of the principles apply to other digital ecosystems as well.
Writing this guide allowed me to create my own plan and upped my game in regard to my security practices in my numeric life. I’m a long-time user of 1Password, a well-known password manager that is at the center of my strategy. During my research, I upgraded to the paid subscription1 of 1Password which helped me improve my security posture in many ways.

This guide is a three parts guide. The first part is about helping people build an emergency kit that will help survivors manage their numeric legacy. Part 2 is about creating and managing the electronic vault. Finally, the third part consists of describing the actual process of using the emergency kit after your dear one passes away2.
Part 1 — The secure envelope
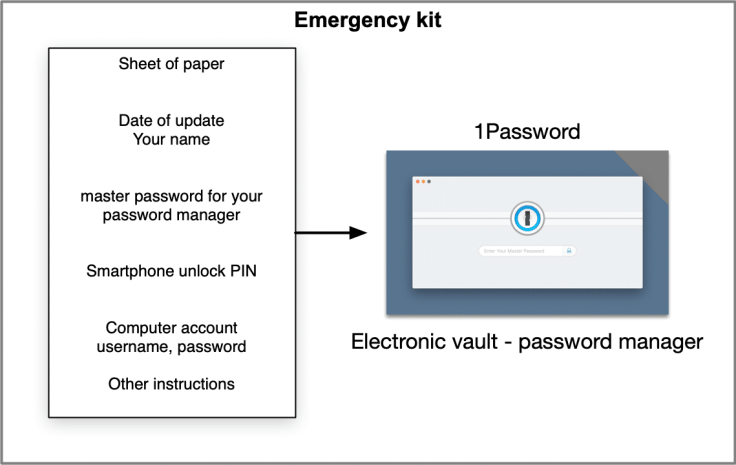
The first thing to do is to create a one-pager document on which you’ll write enough information to kick start the process of taking control of your numeric legacy. That is the sheet of paper that will be put in an envelope. In order to access the digital world, a secure envelope act as the backdoor to this closed world.
In order to prepare the secure envelope, four important questions need answers: which informations should be in it? How should you store them? Where should you put this envelope? Who should know about the secure envelope existence? Let’s look more closely at each question.
What
First, determine what are the minimal pieces of information that will be required to get access to your numeric legacy. The date and the person name you expect to read the document must be there. Describe how to access the electronic vault (required for the next part). Write down the PIN number used to unlock your smartphone or tablet. Write down the username and password of the account used to unlock your computer (if you own one). Never write anything down anything related to your work, as this could violate a corporate security policy. The following list summarizes the minimal information that should be written down.
- Current date
- Your name
- The name of the person you expect to have access to this information
- The PIN used to unlock on your smartphone
- The PIN used to unlock your tablet
- The email address you use the most
- The account information used to open a session on your computer
- The name of the password manager you and where it is located
- The master password required to unlock the password manager vault
How
Your sheet of paper is created in a text editor of your choice and saved on a computer or a tablet. My suggestion is to refrain from using an electronic device like a USB key to be put in the envelope. These devices can fail at the worst moment and may not be compatible with future equipment required to read their content. Why not print the document and store it in the envelope. Simple. Effective. When you are ready to store the envelope, seal it. It’s a good way to detect unwanted breach3. When you need to update the information contained in the secure envelope, first create a new version then destroy the old one with a shredder. Keep all versions of the electronic document, though.
Where
There are many places where the emergency kit envelope can be stored. If you have a safe in a bank, this is probably the most secure way. Alternatively, if you have a safe at home, use it. If you have a physical document filer with personal documents, you can classify the envelope with your other personal papers. You could mention the location of the secure envelope in your will too. Finally, consider storing two copies of the secure envelope, just to be safe against fire or other life disasters. But remember the more copies, the less secure it is.
Who
The secure envelope is as useful as someone knows about its existence. It must be a person you trust the most. Don’t take it too lightly. As you can understand, the content of the secure envelope is the key to your numeric legacy. It can be your husband or wife, your sister or brother, or one of your children.
Part 2 — The electronic vault
Take advantage of this guide to update your security posture and practices. You’ll find instructions on how to use modern security measures like two-factor authentication. If you don’t use a password manager, now is the time to get one.

You need a way to write down your account passwords and other important information in a secure way. Don’t write them on paper 4. You have to be clever, more sophisticated. There are a plethora of password managers on iOS or macOS. Personally, I’m using 1Password and Apple’s iCloud Keychain5. The former has been available for many years. The latter is integrated into Apple’s operating systems. It is very convenient but lacks a few important features usually found in more sophisticated applications. 1Password can store much more information than account passwords. You can store secure notes, credit card information, passport information, etc. As mentioned earlier, 1Password is subscription-based. By subscribing you get secure access to your passwords vault from anywhere on 1password.com6 website.
If you use many web services and have many accounts, I would suggest that you record the most important one first. While doing this exercise, consider closing down accounts that you no longer use, but mark them as such in your password manager. Keeping account history can prove to be valuable, you never know.
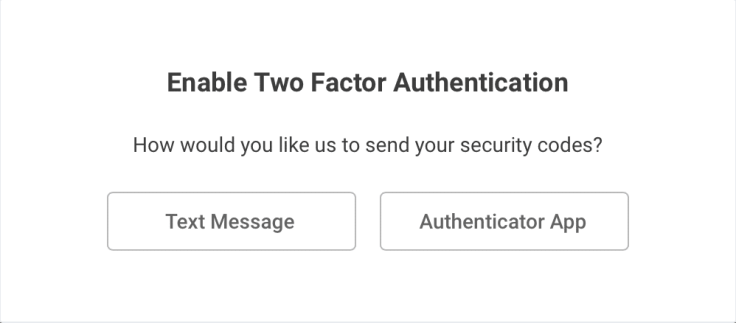
While entering or updating your account information, you’ll get a warning if the website supports two-factor authentication (or 2FA). For each of these warnings, take action and enabled it. Learning about what is 2FA is not in the scope of this guide, though. If you want to learn more about 2FA, read this short guide or a more complete explanation on Wikipedia7. To see which sites support 2FA, see https://twofactorauth.org. Suffice is to say that protecting an account with 2FA is a really good security practice which I encourage you to adopt. While doing so, you’ll need a small application on your iPhone or iPad like Authy8. That’s the one I use and I’m pretty much happy with it.
Don’t forget to look on your iPhone or iPad to see which applications you use and note the ones that require a password as you should record them too. If you are the type of person who uses the same password for many accounts9, say it so in a secure note with your password manager10. That way, if you forget to record an account, your survivor could try to use that frequently used password.
Oh and finally, why not keep a list of your subscriptions in your password manager. These are services that will need to be eventually terminated. Don’t limit yourself and write any pieces of information that you deem important for someone to know when you pass away.
Part 3 — When bad things happen
Death is part of life. It is a sad event. He or she left behind a numeric legacy. You don’t know anything about it, but you are going to find out. Most people don’t care about putting some order into their numeric life and death can happen anytime soon. For those who read this guide and left behind the emergency kit with a secure envelope, they are lucky. Let’s see what could happen when the death strike. As shown in the following diagram, the first stage is the discovery phase of your journey.
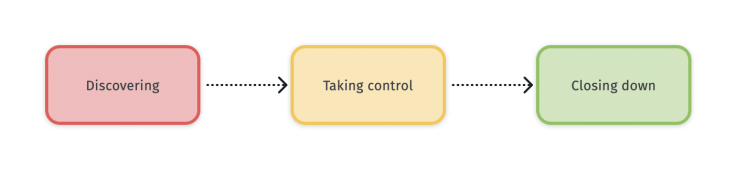
The discovery phase
Where do you start? Use the secure envelope from the emergency kit. You’ll find a sheet of paper with the required account information to get access to the diseased’s smartphone, tablet or computer. Next, you should be able to enter the diseased’s password manager where you’ll find a treasure of security information.
The take control phase
With the secure envelop on hand, you now have a better hand on this numeric legacy. Now, it is time to visit every service starting with the most important ones. If you want to keep them for a while, it might be a good idea to reset the password and change the recovery email address if one is available to one of yours. Many online services allow setting up a recovery email address or phone number on an account. By resetting the password of that account, an email will be sent to the recovering email address. By monitoring the diseased’s mailboxes, you will quickly receive an email containing an URL to trigger the password reset.
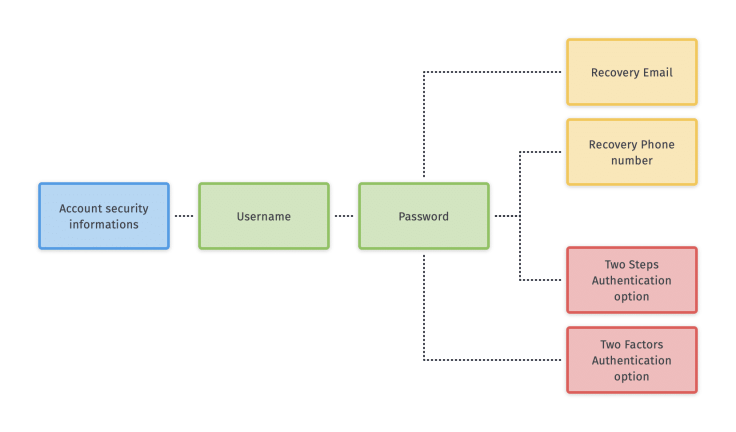
You must keep the mobile phone or tablet of the diseased person for 2SA or 2FA authentication requirements if such security measures were used. Don’t cancel credit cards, monitor them for a few months and see transactions unfold. You will probably make a few discoveries. Also, subscriptions to critical services like password managers like 1Password are required to keep the access to the data they contain.
The close down phase
The final phase is to start closing down each service, one by one. Start with the least important ones. A Facebook account should probably be the last one to be closed. Same for emails and Apple ID accounts. Apple ID, Google accounts should be closed at the very last step. For each of them, you have to make sure that there is no valuable data or information to export first. Not all online services provide a way to export the data. For those that do, the export process is different and takes some time to export and download. The end result is some sort of file which varies in format. There is no standard process yet.
Taking over the numeric legacy of someone is a strange journey. As we proceed, we inherit things that will, in turn, grow our own numeric legacy. Eventually, we’ll have to create an emergency kit too so others can keep memories alive and help pass it along to the next generation.
Concluding words
My goal while writing this guide was for helping others address the challenging task of managing someone’s numeric legacy. With the help of the emergency kit on hand, a kit made of a secure envelope and an electronic vault, it should ease the challenge quite a bit. Hoping that you won’t have to use one anytime soon. Stay safe.
- Yes, I know, you probably hate this business model. ↩
- This is not an easy task. It takes time, but think of this as an investment for your survivors. In fact, it is more like a way of life. ↩
- If such a thing happen, you’ll have to change all your password as soon as possible. Then, try to find the reason why the envelop was opened and by who. ↩
- Only the emergency envelope should contain the minimum required information. ↩
- Why use a separate password manager when Apple’s iCloud Keychain seems to work just fine with websites? One of the missing feature is the lack of password history, just to name one. ↩
- This is by no mean a review of 1Password, but it is certainly an endorsement. ↩
- Don’t mix 2FA with two-steps authentication (or 2SA). It is similar in nature, but 2FA is much more secure than 2SA ↩
- Google Authenticator is another popular, but less appreciated one. 1Password offers this feature too. ↩
- Using the same password for many account is not a good practice. Now is the good time to stop doing that, especially if you are now using a password manager. ↩
- Modern password managers already flag this for you because it is a very very very bad practice. ↩



