Protecting Your Digital Life: Privacy and Security Measures for Apple Users
This article explains all the security features any users of an Apple device can benefit from.

Privacy and security are crucial aspects of our digital lives, and Apple devices offer strong built-in protections that anyone can and should use. Even if you're not technically inclined, there are straightforward ways to safeguard your personal data and privacy. This guide is designed for non-technical users and everyone to read, highlighting essential practices to help you stay safe online by leveraging Apple's powerful yet user-friendly tools.
I wanted to write something easy to understand so that people could easily take advantage of it. Consider looking at the following diagram to get an overview of the building blocks that will increase your security posture. This diagram should help you learn how they relate to your digital ecosystem based on Apple technologies.
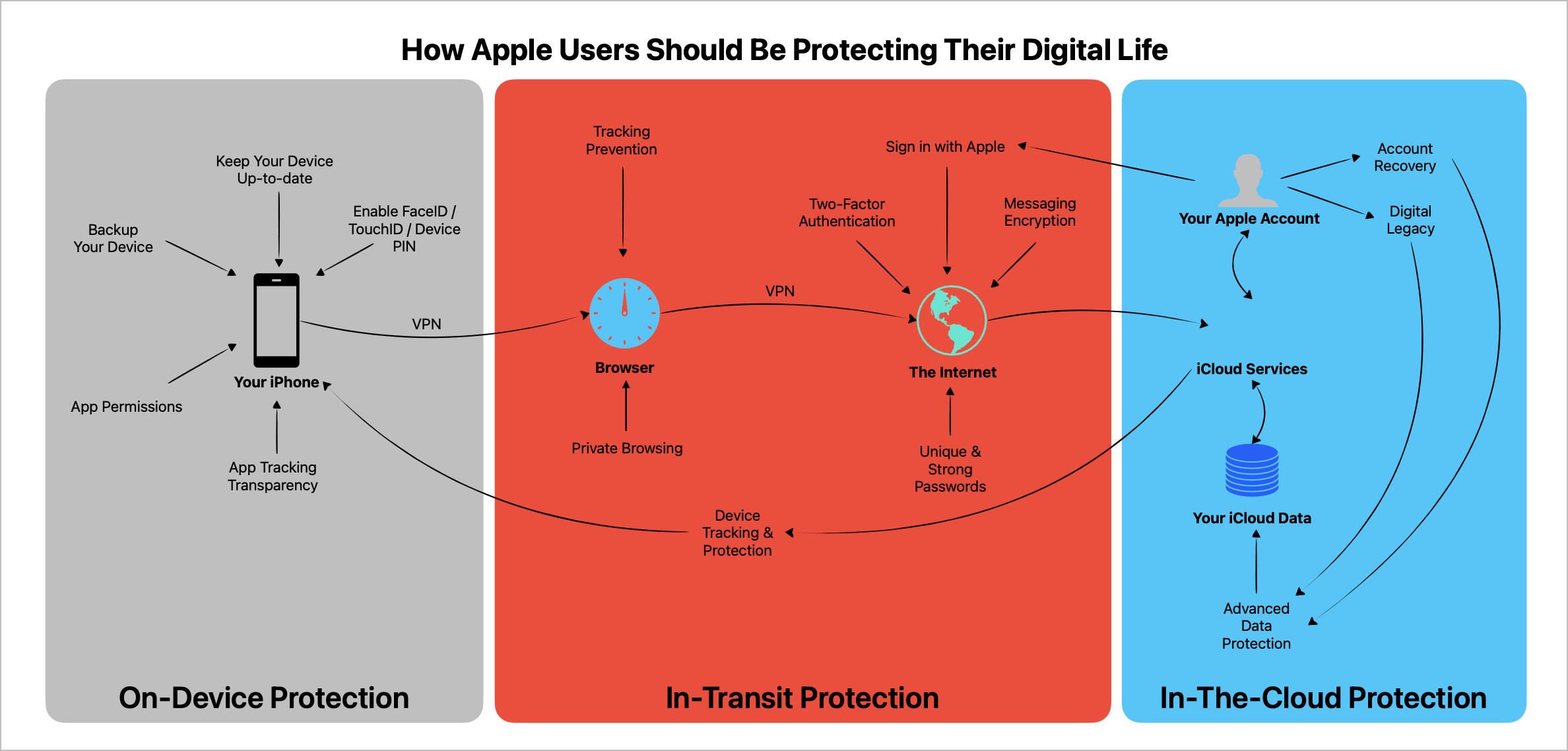
What Is a Security Posture?
In the cybersecurity realm, a "security posture" refers to the overall security status of an organization, system, or individual based on its resources, capabilities, and policies. This concept encompasses the readiness and ability to predict, prevent, and respond to various cyber threats. When applied to an individual, a security posture includes all the measures and practices one adopts to protect their personal digital environment, maintain data privacy, and ensure safe interactions online. These practices involve using strong passwords, enabling two-factor authentication, regularly updating devices and software, and being aware of phishing attempts, among other things.
In the context of Apple users, security posture involves using the built-in tools and resources that Apple provides to enhance digital security. Apple devices generally come equipped with user-friendly features designed to protect personal information, such as biometric authentication (like Face ID or Touch ID), encrypted messaging through iMessage, and privacy settings that limit what apps can access personal data. Even individuals who are not technically inclined can reinforce their security posture by taking advantage of these features. For example, they can easily activate two-factor authentication for their Apple Account to add an extra layer of security or manage their privacy settings to control which apps have access to location data or personal contacts.
By understanding and applying these digital security fundamentals, individuals can significantly enhance their security posture. It is about leveraging tools that are readily available and following best practices to protect one's digital presence effectively. This approach safeguards personal information and provides peace of mind while navigating the digital world.
Now, let’s dig into this in more detail.
Regularly Update Your Devices
Keeping your devices up-to-date ensures you benefit from Apple's latest security enhancements and privacy improvements. Regular updates address known vulnerabilities, significantly reducing your risk from cyber threats, malware, and unauthorized access. Updates often include improvements to device performance and stability alongside critical security patches. Apple's automatic software updates make it easy to maintain optimal security without needing to check for new versions manually. Staying updated is one of the simplest yet most effective ways to safeguard your personal data and device integrity.
If you own an old device, Apple often keep releasing security-related updates and you are good to go, but when Apple stop releasing those updates, consider upgrading your device. Also, if you don’t want to update to the newest major release, Apple makes security-related updates available for the previous major releases. For example, while iOS 18 is the current major release, you can select to stay on iOS 17 and apply the latest minor release if you want. That way, you keep your security posture in good shape.
Physical Device Security
Protecting your devices physically is as important as digital security. Avoid leaving your devices unattended in public spaces to minimize theft or unauthorized access. Consider using privacy screen protectors in public areas to prevent others from viewing your screen. Additionally, be cautious when using accessories or chargers from unknown sources to prevent potential security risks.
Using accessories or chargers from unknown sources can pose significant cybersecurity risks to your digital devices. Firstly, counterfeit or uncertified chargers might not adhere to the stringent safety standards set by manufacturers like Apple, potentially leading to device malfunctions or physical damage. Beyond physical risks, these unauthorized accessories can also harbor malicious software or hardware designed to compromise your device. For instance, they could be used to deliver malware, which might allow attackers to gain unauthorized access to your device, steal personal data, or even control your device remotely. These risks underscore the importance of using only trusted and certified accessories. There are documented cases of malicious charger cables that proved to pose serious security risks. It’s not science fiction, it’s real.
“The Forbes article warns Apple users about the risks of using unfamiliar charging cables, highlighting a specific type known as the “O.MG Cable.” This cable resembles standard USB-C or Lightning cables but contains embedded hardware that can remotely access and control connected devices over Wi-Fi. Once plugged in, it can execute commands, potentially compromising personal data and device security.”
Use Strong and Unique Passwords
Protect your devices and accounts by choosing strong, unique passwords and passcodes. Avoid using simple or easily guessable unlock codes like "123456" or birth dates. Instead, enable Touch ID or Face ID whenever available for enhanced security. Apple doesn’t keep your fingerprints; don’t worry about that.
Apple provides tools like iCloud Keychain to help create and securely store complex passwords, making your accounts harder to compromise.Those passwords then sync across all your Apple devices, offering seamless protection. Apple recently created a dedicated password management app called “Passwords” that is very capable and free to use. It's available in iOS 18, iPadOS 18 and macOS Sequoia. Consider giving it a look. Other password management apps or services includes 1Password, Bitwarden, Keeper, just to name a few of them. Here’s an article comparing them.
Enable Two-Factor Authentication
Use two-factor authentication (2FA) whenever possible to add an extra layer of security to your accounts. Apple’s built-in two-factor authentication protects your Apple Account by requiring a second form of verification—typically a code sent to your trusted devices. This significantly reduces the risk of unauthorized access, even if your password is compromised. Apple Passwords app supports enabling two factors authentication for accounts that support it. I highly encourage you to us this because it’s more secure and for many websites, the integration with Apple Safari is seamless. Give it a try.
“2FA stands for two-factor authentication. It is an extra layer of security used to ensure that only the person who owns an account can access it, even if someone knows the password. Two-factor authentication typically requires a password and a second piece of information, such as a code sent to a phone, to verify the user's identity.”
Use "Sign In With Apple" for Enhanced Privacy
Using "Sign In With Apple" provides significant privacy and security advantages over traditional email and password authentication. This feature allows you to sign in to apps and websites quickly and securely without sharing your personal email or creating multiple passwords. Apple generates unique random email addresses to keep your personal email private, helping reduce spam and enhance your online privacy.
Complementary to this, Apple Passkeys offer a secure, passwordless authentication method that uses biometric verification (Touch ID or Face ID) for accessing apps and websites. While "Sign In With Apple" simplifies registration and keeps your email private, Passkeys completely eliminate the need for passwords, providing an even higher level of security and convenience. Together, these two methods greatly reduce your vulnerability to password-related threats, making your digital experience both safer and easier.
Pay attention from time to time to the Apple device account list, where you’ll see a list of all your devices where you signed in. Do you recognize all the devices in that list? If so, remove them as soon as possible.
Prepare for Account Recovery
It's essential to have measures in place to recover your Apple Account if you forget your password. An Apple Account always have a password, even if you use Passkeys. Apple provides an Account Recovery option that allows you to designate trusted contacts who can assist you in regaining access. Alternatively, you can set up a Recovery Key as an additional layer of security, ensuring you can quickly and securely regain control of your account.
A recovery key serves as an additional security measure for your Apple account, providing you with a backup option to regain access if you ever forget your password or lose access to your trusted devices. The recovery key is a randomly generated 28-character code that you must keep safe and accessible, as Apple does not store a copy of it. The purpose of the recovery key is to ensure that you have a secure and private method to reclaim control of your account. Setting up a recovery key strengthens your account's overall security and protects against unauthorized access. Remember that if you enable a recovery key, you'll be responsible for maintaining access to it, as neither Apple nor anyone else can help you recover your account if both your password and recovery key are unavailable.
To add recovery contacts to your Apple account, follow these steps:
- Open Settings: Begin by opening the Settings app on your iPhone or iPad.
- Tap on Your Name: At the top of the Settings menu, you'll see your name or Apple ID. Tap on it to access your Apple ID settings.
- Select Password & Security: Within your Apple ID settings, tap on "Password & Security" to proceed.
- Choose Account Recovery: In the Password & Security section, look for "Account Recovery" and select it.
- Add Recovery Contact: Tap on "Add Recovery Contact." Follow the on-screen instructions to choose a trusted contact from your list of contacts. This person should ideally be someone you trust and can easily reach if you need help recovering your account.
- Notify Your Contact: Once you've added the contact, they will receive a notification to confirm that they've been added as a recovery contact.
By following these steps, you enhance your security posture by ensuring you have a trusted person who can assist in regaining access to your Apple account if needed.
Set Up Your Digital Legacy
Preparing your digital legacy is important to ensure your family or trusted contacts can access your devices and personal data after you pass away. Apple's Digital Legacy feature allows you to designate specific individuals as legacy contacts. These trusted contacts receive secure access to your devices, photos, notes, messages, and other critical information stored in your Apple Account after your passing. Setting this up helps ensure that your digital memories, documents, and important data remain accessible to those who matter most during challenging times, while also ensuring your privacy and security remain respected.
You can add up to five Legacy Contacts from your Apple devices:
On iPhone or iPad:
- Open the Settings app.
- Tap your name at the top to access your Apple ID.
- Select Password & Security.
- Tap Legacy Contact and then Add Legacy Contact.
- Choose a contact from your Contacts list or Family Sharing group, or enter their email/phone number.
- Share the Access Key with the contact via Messages or print/save it for future use.
Enable Device Tracking and Protection Features
Apple’s "Find My" feature is essential for locating lost or stolen devices. Activating this feature helps protect your data by allowing you to remotely lock or erase your device, minimizing unauthorized access. "Find My" also uses end-to-end encryption, ensuring your location data remains private. Additionally, Activation Lock, part of "Find My," makes stolen devices unusable by unauthorized users. Activation Lock requires your Apple Account credentials to disable "Find My," reactivate, or erase the device, making it significantly harder for thieves to profit from stolen devices. It also provides peace of mind that your personal information won't fall into the wrong hands, even if the device is physically compromised.
Consistently Back Up Your Data
Regularly backing up your data protects against data loss from device theft, accidental deletion, or hardware failure. Apple's iCloud Backup simplifies this process, providing secure, encrypted backups. You can select exactly which data—such as photos, messages, documents, or apps—you wish to include or exclude from backups. This granular control allows you to minimize storage space consumption in your iCloud account while ensuring critical data remains protected.
Additionally, for Mac users, Time Machine offers a reliable backup solution using external physical drives, which should ideally be stored in safe, secure places to prevent theft, damage, or unauthorized access. This approach also provides customizable backup options to fit your specific needs, ensuring you have full control over which data is protected and how frequently backups occur.
Enable Advanced Data Protection
Apple’s Advanced Data Protection provides end-to-end encryption for your iCloud data, ensuring only you can access your sensitive information. This powerful, free feature significantly enhances your privacy by protecting photos, notes, messages, backups, and more from unauthorized access, even in the event of a security breach. While this feature might not be available in all countries or supported on older devices running earlier operating systems, you should seriously consider enabling it wherever possible for the ultimate protection of your data.
You must have a valid Recovery Contact or a Recovery Key set up before enabling Advanced Data Protection.
- Recovery Contact: A trusted person who can help you recover your data if you lose access.
- Recovery Key: A 28-character code you must securely store. If you lose both your devices and recovery key, Apple cannot recover your data.
When you enable Advanced Data Protection, iCloud web access must be disabled for additional security. This means you won't be able to access your iCloud data through a web browser, adding an extra layer of protection against unauthorized access. While this may limit some convenience, the trade-off results in a more secure environment for your personal information. You can learn about this in this Apple support article.
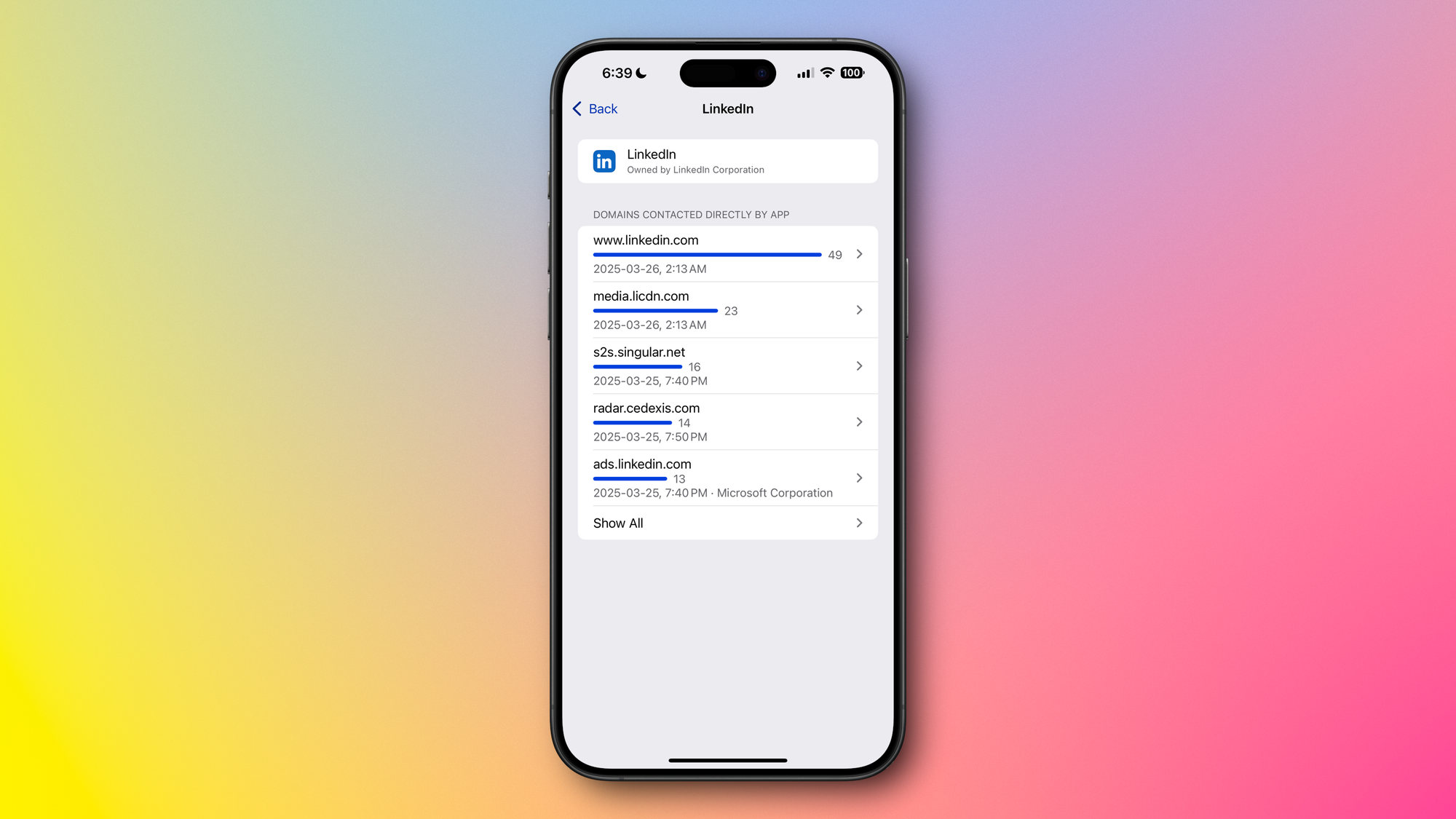
Manage App Permissions Carefully
Be cautious about granting apps unnecessary permissions. Regularly review and limit access to sensitive information such as your location, contacts, photos, camera, and microphone. Apple’s App Privacy Report feature gives you detailed insight into how frequently and when specific apps access sensitive information or device features, such as your location, contacts, camera, microphone, or network connections. By reviewing this report, you can easily identify apps that might be unnecessarily accessing your personal data, enabling you to better manage app permissions and significantly enhance your privacy and security.
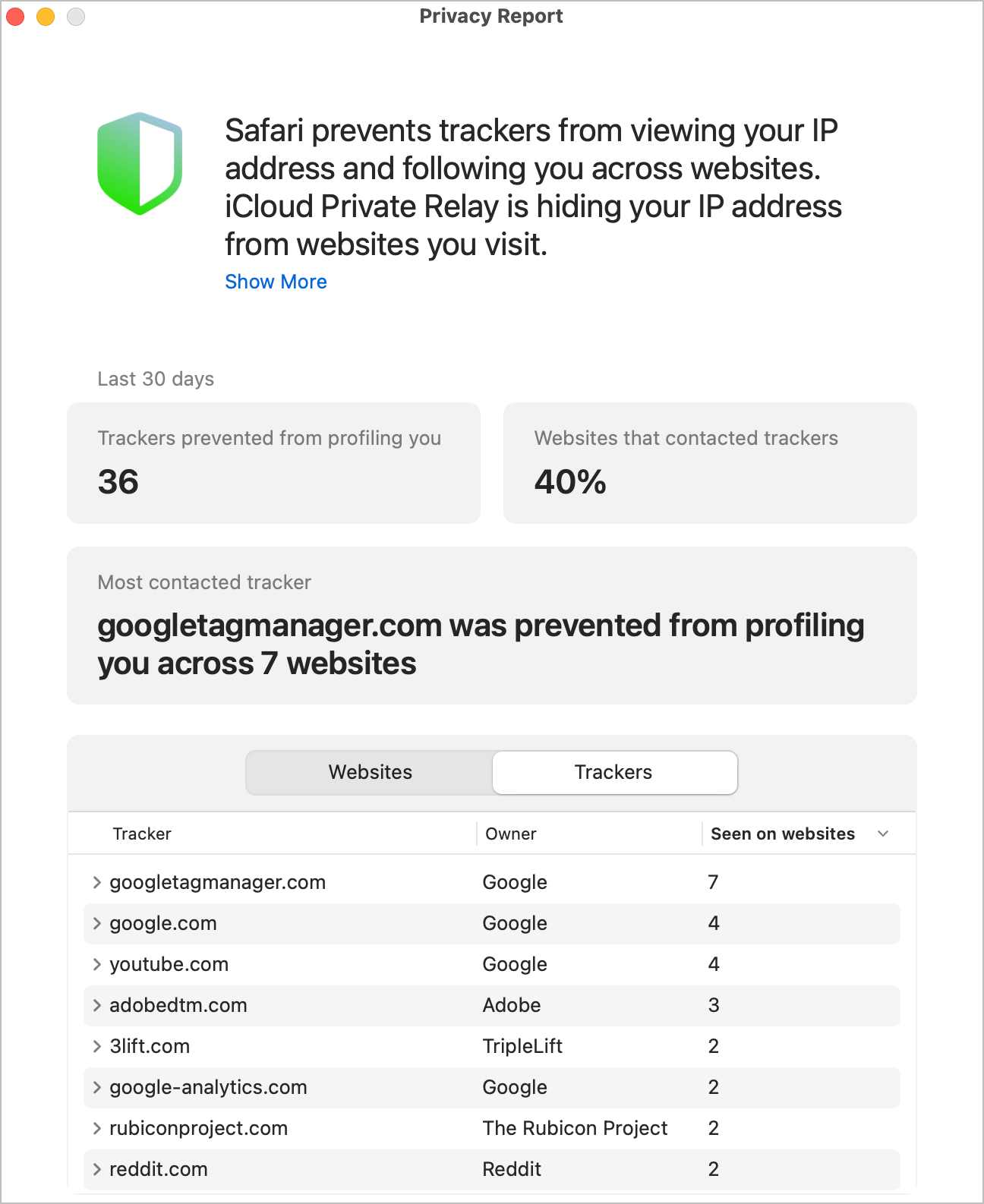
Protect Your Browsing Activity
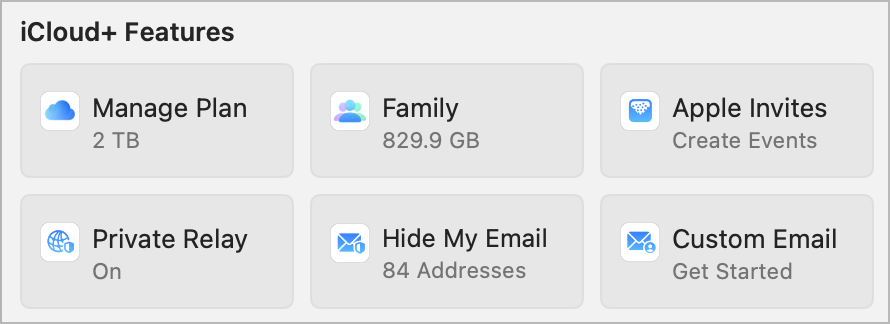
Safari, Apple’s built-in browser, provides robust privacy features like Intelligent Tracking Prevention, which automatically blocks trackers and prevents advertisers and websites from following your online activities across the web. This helps maintain your online anonymity and reduces targeted advertising. Additionally, iCloud+ includes Private Relay, a privacy-focused service that encrypts your internet traffic and hides your IP address. Private Relay routes your internet requests through two separate servers, ensuring neither Apple nor your internet provider can view your browsing activity, greatly enhancing your privacy and protection against network tracking.
Using Safari's Private Browsing mode is another effective way to enhance your privacy online. When enabled, Private Browsing prevents your browser from recording your browsing history, searches, and cookies, ensuring that no trace of your activity remains on your device. While Private Browsing doesn't make you completely anonymous to websites or your internet provider, it provides an additional layer of privacy protection, especially useful when accessing sensitive information or when using shared devices.
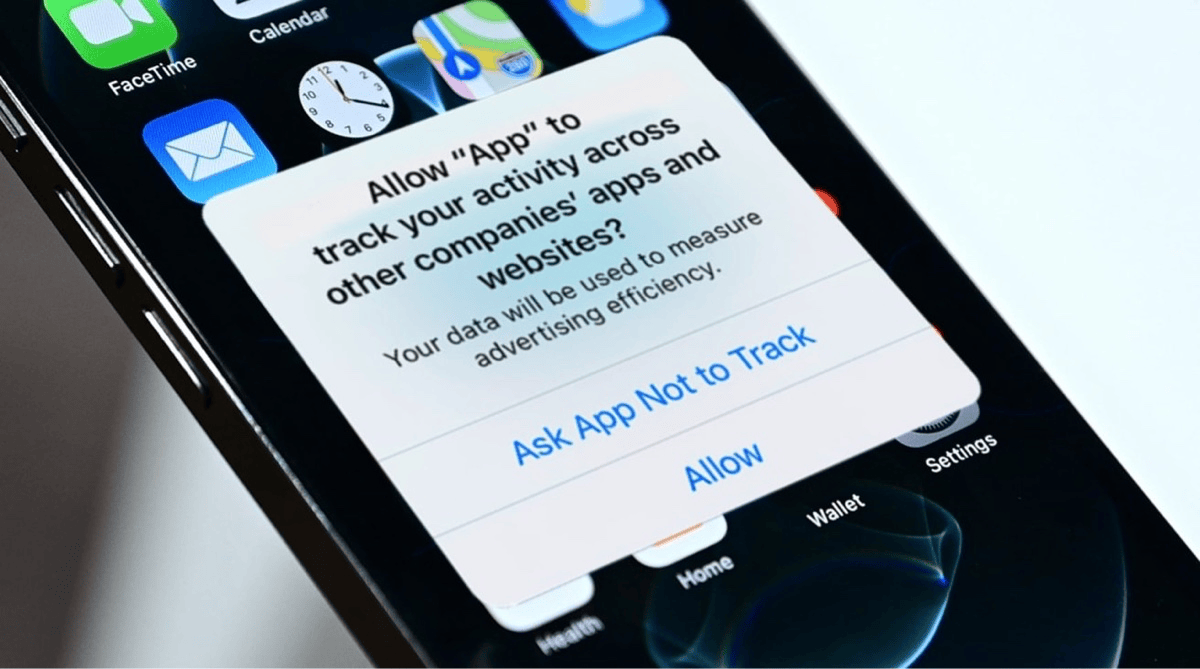
Understand App Tracking Transparency
Apple's App Tracking Transparency, often referred to “ATT”, empowers you to control which apps can track your activity across other apps and websites for targeted advertising or data-sharing purposes. It'a different feature than Intelligent Tracking Prevention in Safari. With App Tracking Transparency, apps must explicitly request your permission before tracking you, allowing you to decide which apps, if any, you wish to grant this access. This feature significantly reduces unwanted tracking, protects your personal information, and enhances your online privacy. I always answer “Ask App Not to Track”.
Secure Your Connection on Public Networks
When using public Wi-Fi, your data could be vulnerable to interception. Although it's an older technology, a trusted VPN provides a highly secure and private experience by encrypting your internet connection and hiding your online activity. Apple’s iCloud+ Private Relay offers additional modern protection by routing your internet traffic through two separate relays, further safeguarding your privacy even on unsecured networks. Using both technologies can significantly enhance your online safety and privacy.
Use iMessage for Secure Communication
Using Apple's iMessage service provides significant security and privacy advantages compared to standard text messaging. iMessage encrypts your messages end-to-end, ensuring only you and your intended recipient can read your conversations. Additionally, Apple has introduced iMessage Contact Key Verification, a feature that enables users—particularly those at higher risk—to verify they are communicating securely with the intended person and not an unauthorized third party. This adds another layer of security, helping you confidently protect your sensitive conversations from potential eavesdropping or interception.
Stay Alert to Phishing and Scams
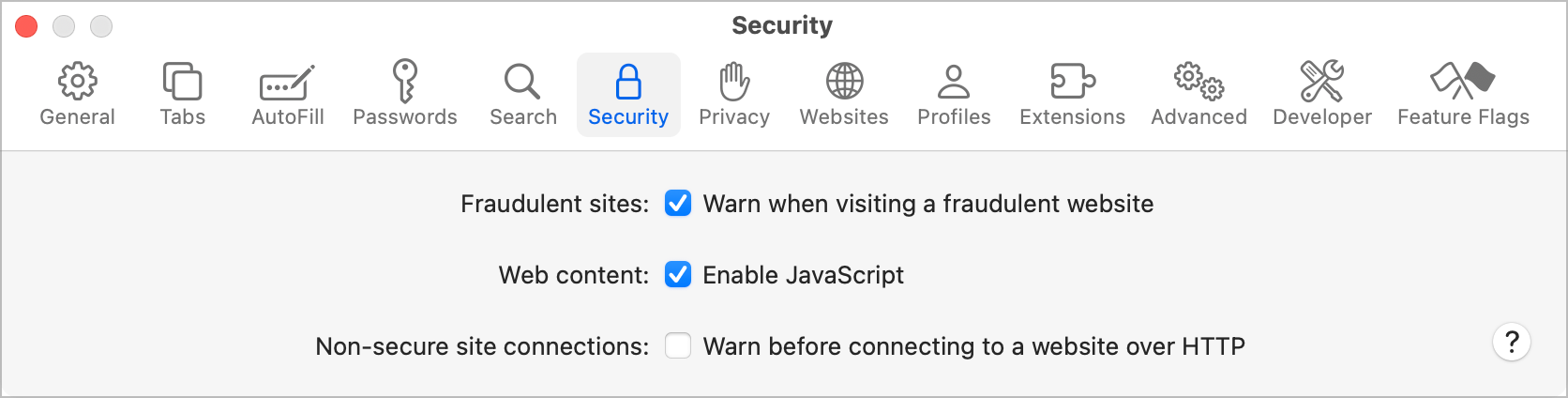
Awareness of phishing scams—deceptive emails, messages, or links designed to trick you into revealing personal information—is vital. Apple provides built-in protection against known phishing sites through Safari's Fraudulent Website Warning, a feature designed to protect you by identifying and alerting you when you attempt to visit deceptive or malicious websites. This helps prevent phishing scams, malware downloads, and other potential online threats by providing a clear warning, allowing you to navigate away from harmful content safely. Remember, Apple will never ask for your sensitive details via unsolicited messages.
Get to know and control your data
If you want to know what Apple knows about you, you can visit privacy.apple.com website. From there, you’ll be able to download a copy of everything Apple is collecting about you. If you plan of moving some of your data to a third-party service, you’ll probably be able to do so from this website, too (like migrating to Google Photos). Finally, if for any reason you want to disable your Apple account or even delete it, that’s the place to go, too.
Embrace a Privacy-Focused Mindset
Maintaining privacy and security on your Apple devices comes down to staying informed and practicing good digital hygiene. By consistently using Apple's privacy tools—such as iCloud+, App Privacy Reports, Advanced Data Protection, Digital Legacy, Activation Lock, and device encryption—you significantly strengthen your digital security and safeguard your personal privacy.
Many Apple-provided services and features are also available from third-parties. You can have a great security posture by using other solutions for browsing the web, storing your passwords. Some features are unique to Apple and benefit from a tight integration with iOS, macOS and Safari browser. If you want to know more about Apple’s unique privacy-related features, consider visiting this Apple mini website.
I hope you found this article informative. If you enjoy my work and want to support what I do, you can buy me a coffee on Ko-fi or send a little something via PayPal. Every bit helps and is truly appreciated—thank you for your support!



